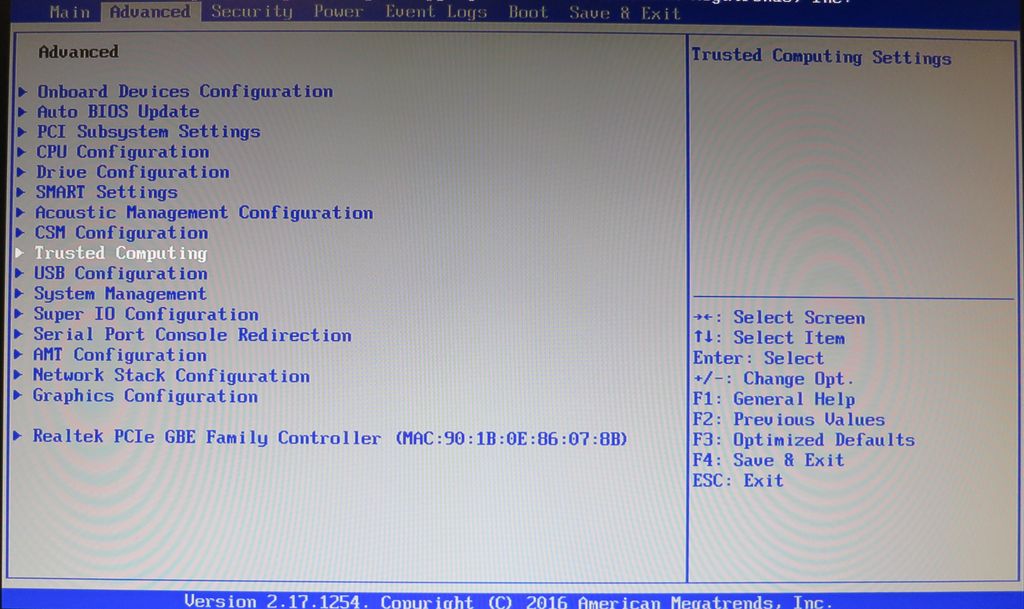
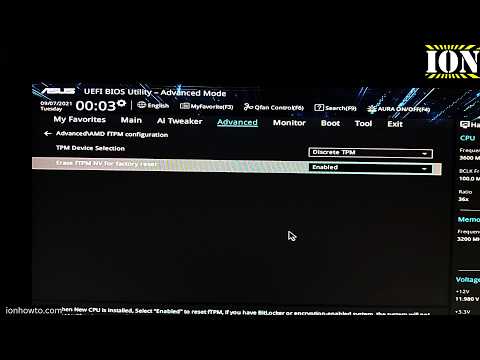
End-users may find themselves in a situation where TPM cannot be enabled in firmware despite being technically supported. Absent a physical TPM 2.0 module, there may not be a way to enable TPM 2.0 on such a machine. This may or may not matter, depending on whether Microsoft will enable upgrades for your platform in the first place. This may be part of why Microsoft locked out older systems; it's possible that OEMs only began shipping all of their systems with UEFI-accessible TPM options when AMD launched Zen+ and Intel was shipping Coffee Lake. Trusted Platform Modules are computer chips that securely store artifacts used to authenticate the platform.
These artifacts can include passwords, certificates, or encryption keys. You can also use a TPM to store platform measurements to make sure that the platform remains trustworthy. For servers configured with a Trusted Platform Module, TPM enables the firmware and operating system to take measurements of all phases of the boot process. For information on installing and enabling the TPM module option, see the user documentation for your server model. Firmware TPM enables more devices, including lower-cost and lower-power systems, to support the same root of trust concepts enabled by hardware-based TPM.
This is especially helpful in the industrial PC space as it lets organizations establish the same, rigorous levels of security on endpoints and gateways as on desktop hardware. These firmware TPM solutions also meet Microsoft's Windows 11 requirements. That means systems with Intel PTT or AMD's fTPM solution should be in the clear for Windows 11 support. Microsoft's Windows 11 website lists the minimum system requirements, with a link to compatible CPUs and a clear mention that a TPM 2.0 is required at a minimum. Note that IEEE 1667 was installed in my second PC, it was shown as a hub with child devices including the TCG storage that Windows 10 silently dropped in a recent build. Microsoft called that "Enhanced Storage devices", but this is wrong and larger than that.
Its promise of security is completely fake in all aspects. Gigabyte sent me a version version which is not even listed in their public website, supposed to fix the issue. However even if now the TPM was recognized, it was working only once, then on the next boot there's a recovery process. This chip is usually embedded on the motherboard, and it stores, generate, and protects encryption keys. Microsoft made this chip a prerequisite for upgrading to Windows 11, and if you are interested in this upgrade, you want to make sure that your device meets the requirements.
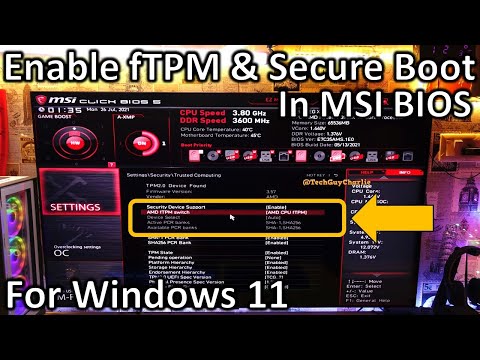
Sometimes, TPM is disabled, which may give you the impression that your device is not ready for the Windows 11 upgrade. The great news is that you can easily enable it through UEFI. There are two ways that you can go to the UEFI mode and enable TPM. Now from all tech lover to a regular user of windows wants to install Windows 11 on their PC or Laptops and here things get twisted. Actually, this new version of windows is required an advanced type security module as a Windows 11 minimum requirements. This security module is called Trusted Platform Module or TPM.
Due to the lack of this module, PC Health Check App show this error – "This PC can't run Windows 11" while checking compatibility. Now, this error became a headache for all Microsoft WIN 11 lovers around the world. If you are one of the users who gets bothered with this TPM 2.0 Chip issue of Motherboard then stop worrying and read the solution below. UEFI benefits extend beyond memory and compatibility improvements. Limitations in MBR-based boot processes are resolved with the UEFI's use of the GUID Partition Table .
The GPT uses globally unique identifiers to address partitions, allowing booting from disks as large as 9.4 ZB [9.4 x 1021 bytes] . Further, the UEFI allows more platform boot options, including network boot capabilities, and can act as the foundation for extended boot loaders. Storage limitations disappear, and boot processes can retrieve data and program modules from anywhere on installed storage. The Trusted Platform Module is a component of most modern computer systems. It is used to help assure the integrity of the platform.
It is used as part of the secure boot process to store and report on certain security metrics during the boot process. On some systems it is also used to securely store a full-disk encryption key. A Trusted Platform Module chip is an essential piece of hardware that is a prerequisite for a Windows 11 Upgrade. If you have a relatively new computer, it is most likely that it has a TPM chip. However, even if your computer has a TPM chip, it doesn't mean it is enabled. This TPM chip is not only essential for a Windows 11 upgrade.
You also need it for security features like BitLocker and device encryption. In this tutorial, I will show you how to enable TPM 2.0 Chip on your PC if it's supported. Windows 11 now lists TPM 2.0, Secure Boot, and UEFI mode as mandatory options to run it.
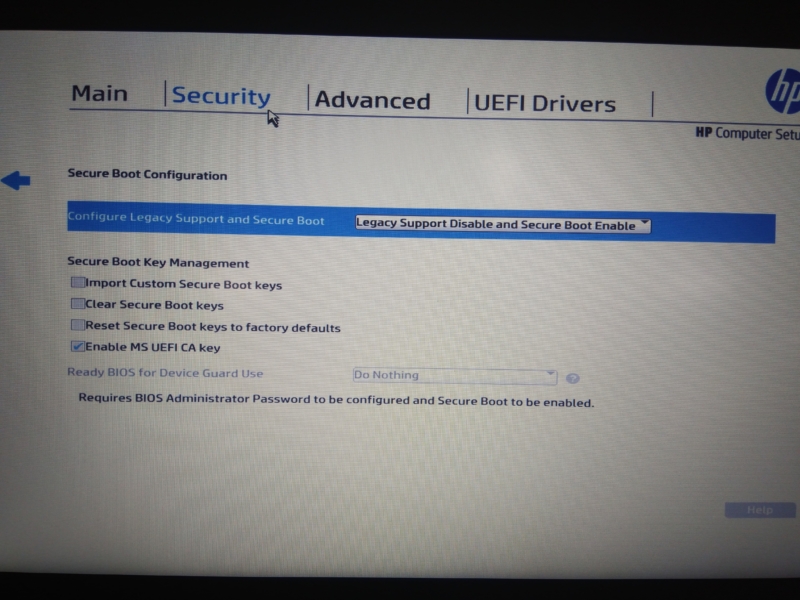
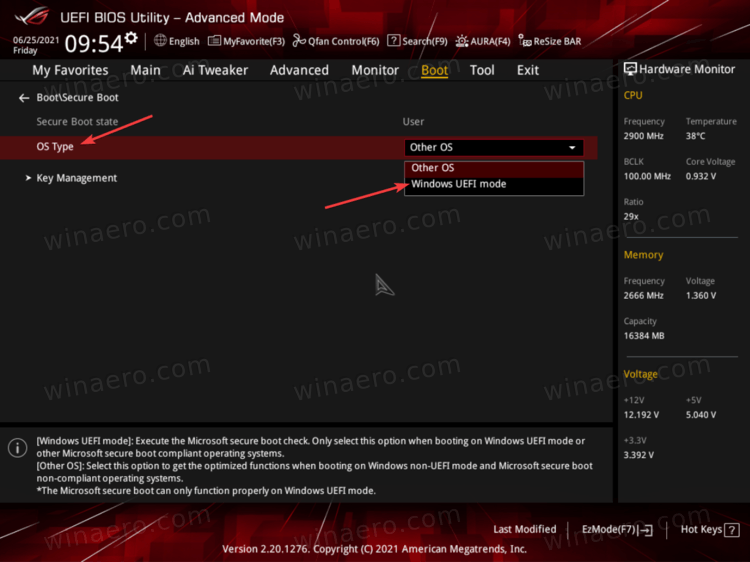
While modern motherboards support all three of those, for some reason, manufacturers ship their products with TPM and Secure Boot disabled by default. Microsoft has made a new tool for checking Windows 11 compatibility. If Trusted Platform Module and Secure Boot are disabled on your machine, the compatibility check tool will tell your PC is not eligible to run Windows 11, even with the newest hardware. If you previously confirmed that secure boot is supported on your hardware, all you need to do is enable it from your BIOS or UEFI settings. This article covers nothing, I guess I missed the " fix " this just added to my frustration! By typing tpm.msc I was told that I had the 2.0 requirements back to health check and no, processor not supported.
There is a tpm that is enabled and nothing I can change in anyway. Microsoft currently requires all Windows 8 certified platform vendors to provide secure boot functionality. While this might work fine for Microsoft and Apple, free OS vendors are not happy. Linux implementations, for example, often do not include signing. Obtaining and managing code certificates is difficult, if not impossible, for decentralized and underfunded coding operations. While this is not typically a big problem for business desktop and mobile computing devices, it can cause problems for more technical users.
Further, it can possibly affect use of Linux-based appliances. With the announcement of Windows 11, there are minimum hardware requirements. One such requirement includes a Trusted Platform Module 2.0, which has taken many users by surprise. This means that computers after 2015 will be able to install Windows 11, but older PCs and laptops will not. It was at the end of 2014 that the TPM version 2.0 began to be introduced into motherboards and processors.
In addition, on many motherboards and processors, it can be disabled by default in the BIOS. That's partly because early versions of the PC Health Check app, which is Microsoft's downloadable tool that tells you if your hardware qualifies for the upgrade, simply threw an error if TPM wasn't enabled on your device. Fortunately, the most recent version will tell you if TPM is the problem. You might run into this issue if you built your PC yourself or got someone else to do it for you. Many motherboards are TPM compatible, but some gaming motherboards skimped on the feature in favor of other bells and whistles.
The TrueCrypt disk encryption utility, as well as its derivative VeraCrypt, do not support TPM. The original TrueCrypt developers were of the opinion that the exclusive purpose of the TPM is "to protect against attacks that require the attacker to have administrator privileges, or physical access to the computer". The attacker who has physical or administrative access to a computer can circumvent TPM, e.g., by installing a hardware keystroke logger, by resetting TPM, or by capturing memory contents and retrieving TPM-issued keys. As such, the condemning text goes so far as to claim that TPM is entirely redundant. The VeraCrypt publisher has reproduced the original allegation with no changes other than replacing "TrueCrypt" with "VeraCrypt". The author is right that, after achieving either unrestricted physical access or administrative privileges, it is only a matter of time before other security measures in place are bypassed.
However, stopping an attacker in possession of administrative privileges has never been one of the goals of TPM (see § Uses for details), and TPM can stop some physical tampering. The primary scope of TPM is to ensure the integrity of a platform. In this context, "integrity" means "behave as intended", and a "platform" is any computer device regardless of its operating system.
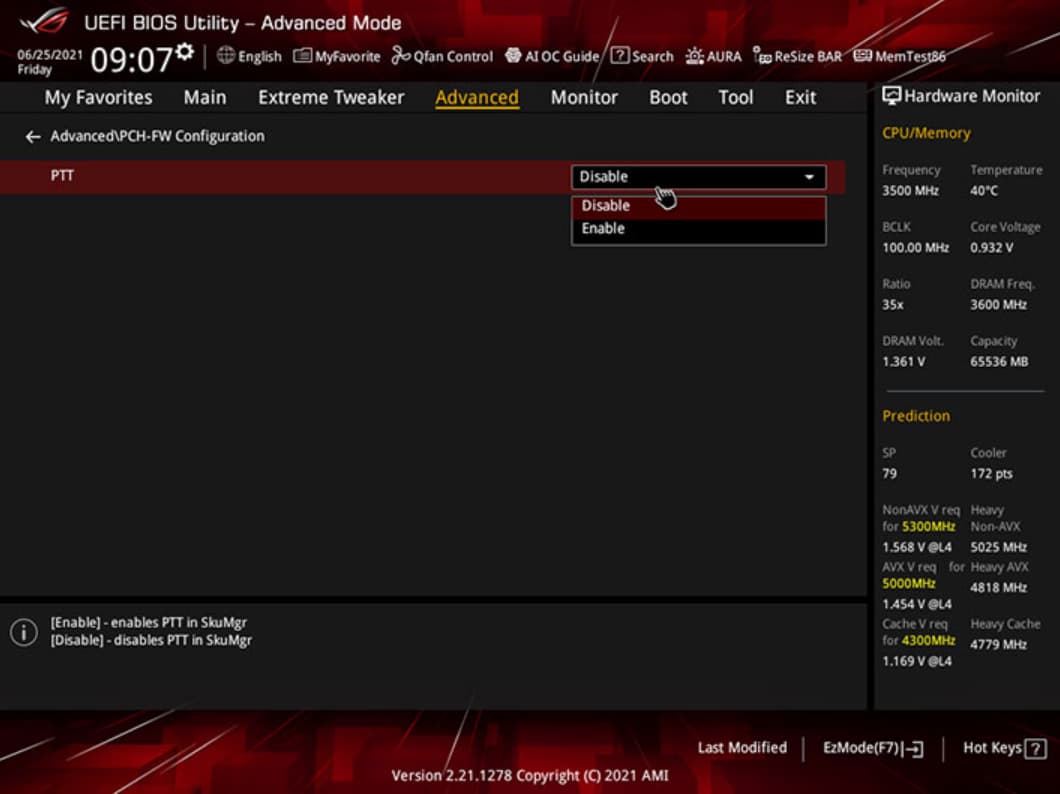
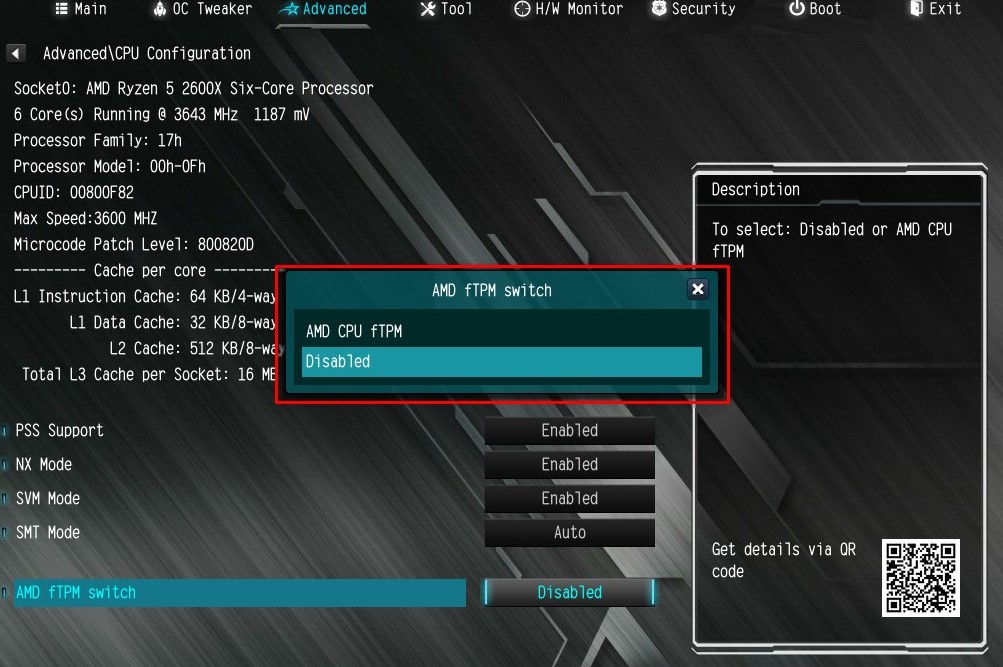
This is to ensure that the boot process starts from a trusted combination of hardware and software, and continues until the operating system has fully booted and applications are running. Microsoft has a habit of struggling to move Windows into the future in both hardware and software, and this particular change hasn't been explained well. While Microsoft has required OEMs to ship devices with support for TPM chips since Windows 10, the company hasn't forced users or its many device partners to turn these on for Windows to work. That's what's really changing with Windows 11, and combined with Microsoft's Windows 11 upgrade checker, it has resulted in a lot of understandable confusion. So, if you don't have a hardware TPM chip, there may be an option to enable fTPM. But it's not as simple as buying a TPM 2.0 add-on module and plugging it into the header.
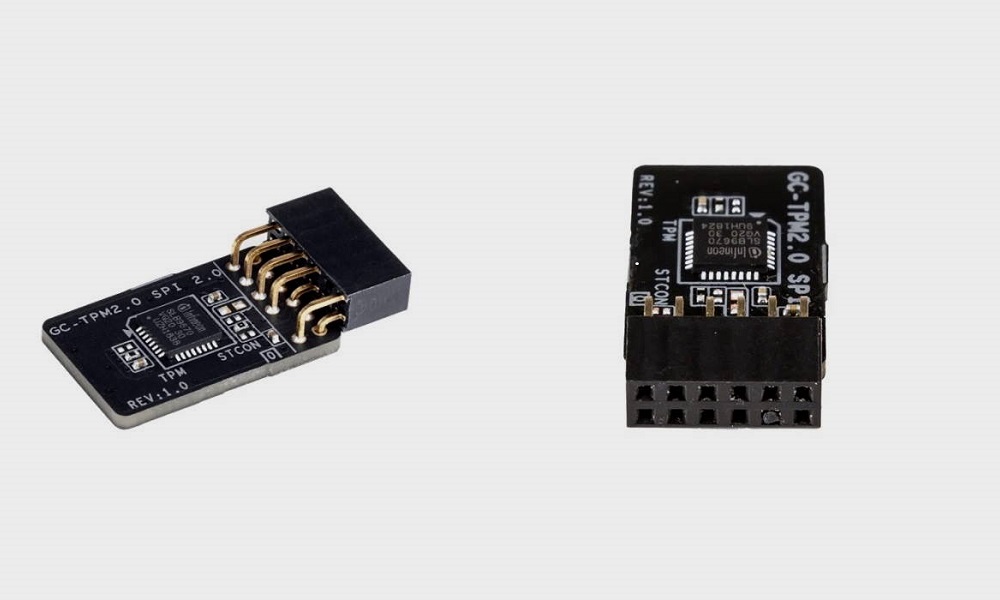
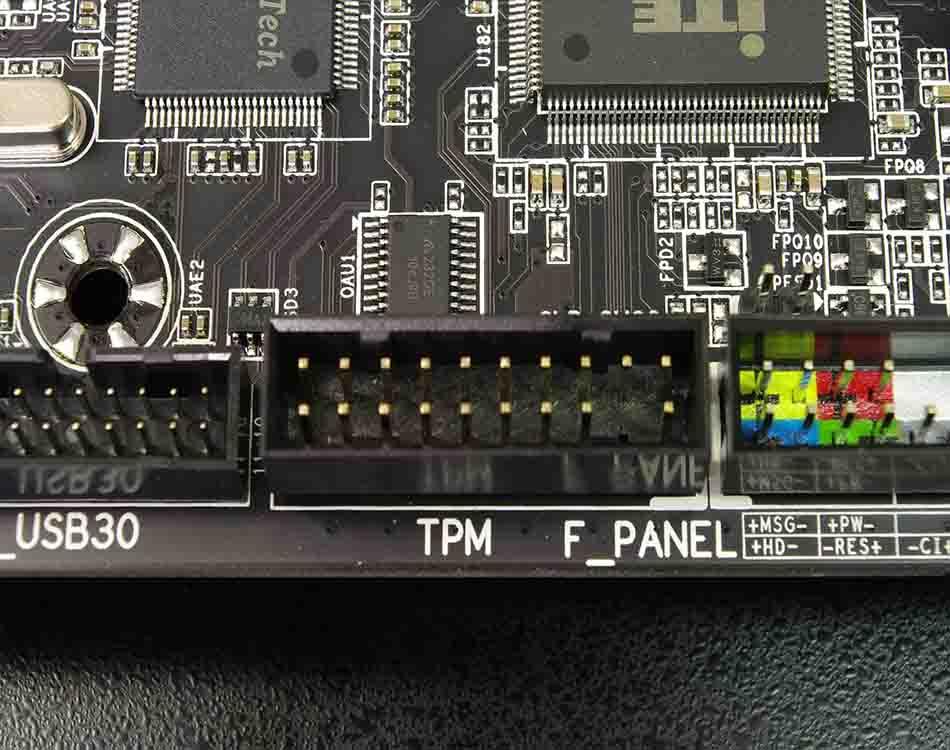
Even if you've got a hardware TPM installed in your home-built computer, you'll need to ensure that it's properly set up in the BIOS for the Windows operating system to recognize it. This process varies widely based on which motherboard and CPU you're using. Even Microsoft acknowledges that turning on TPM isn't necessarily a straightforward process. Microsoft VP of Product Management Steve Dispense suggests that it may be necessary to enable a setting like Platform Trust Technology in the BIOS of Intel-based computers, or fTPM for AMD-based ones. If you built your own desktop PC in the last few years and you're comfortable tinkering with hardware and software security settings in the system's BIOS, you can probably add a discrete TPM 2.0 chip to your motherboard. Many motherboards come with a cluster of header pins clearly labeled "TPM." And, as ExtremeTech notes, you can pick up a TPM module for some motherboard models for less than $50.
However, it is noteworthy that many of the default features being deployed in Windows 11 are available as options in Windows 10. In some cases, getting these more advanced levels of security is just a matter of turning them on. In other cases, your PC's hardware may be too old to handle the new security requirements.
In some cases, especially if your PC was purchased in the past few years, these advanced security settings may be installed and active in the background right now. Windows 11 requires a Trusted Platform Module 2.0 as part of its hardware requirements, but only a very select handful of people will ever need to buy a physical module for their motherboard. Chances are extremely high you don't need one—the vast majority of users can use firmware TPM instead, and everyone else with unsupported hardware is better off running Windows 10 as it is. But if you're determined to seek one anyway, having less competition is a good thing. In addition to PCRs, module storage consists of VRAM and NVRAM (non-volatile memory) (Du, Li, & Shen, 2011). NVRAM contains hardware-protected root of trust data necessary to execute and assure boot path measurements.
In addition, it contains certificates necessary for attestation of signed operating system files and firmware. Conversely, VRAM contains command parameters and is subject to operational changes. Each of these components, or component groups, plays an important UEFI support role.
The RSA Engine can create one-time symmetric keys of up to 2048 bits. It is used during key wrapping operations, digital signing, and encrypting large blocks of data. The SHA-1 (or SHA-256) engine hashes large blocks of data.
RNG is a module's random number generator used to generate keys. The AIK is bound to the platform on which the module resides. It is an asymmetric key pair that attests to the validity of the platform's identity and configuration. There are 24 Platform Configuration Registers , many of which are used to store measures created during the UEFI boot process. PCRs are write-only and cleared only on platform reset.
Does Tpm 2 0 Require Secure Boot To change the boot mode highlight the boot mode option then press enter key, now choose UEFI from the options. (Use the up and down arrow keys to select UEFI and hit enter to select the option. TPMs are controversial among security specialists and governments. An updated and enabled TPM is a strong preventative against firmware attacks, which have risen steadily and drawn Microsoft's attention.
However, it also allows remote attestation and may restrict the kinds of software your machine is allowed to run. TPM-equipped machines generally aren't shipped in countries where western encryption is banned. In Russia, TPM use is only allowed with permission from the government. It ensures the integrity of a platform over the internet or operating system. To ensure that it is functioning, the TPM checks the process of booting and its authority via hardware and software systems.
The TPM also contains configuration registers for storing and reporting the information securely. Not all systems that technically support TPM 2.0 can enable it. This depends on the make and model of your computer, but OEMs may not enable it.
Getting TPM 2.0 up and running on a system that hasn't previously used it isn't impossible, but it should be approached with caution. If you installed Windows under BIOS instead of UEFI, there's no simple way to convert to a TPM-enabled Secure Boot configuration. There is a way to do so, discussed by various commenters in this Ars Technica conversation thread. The linked article covers how to build a proper Windows 11 VM with TPM 2.0 enabled. Microsoft isn't just limiting installation based on the presence or absence of TPM 2.0.
The Surface Studio 2 is TPM 2.0-enabled, but uses a Core i7-7920HQ processor based on Kaby Lake. According to Microsoft's support documents, no Intel CPU earlier than 8th Gen will support Windows 11. No first-generation Ryzen or earlier CPU is listed as compatible with Windows 11. If you don't have access to the Windows 10 desktop, or this is a new computer, you can access the UEFI settings to enable a trusted platform module during the startup process. The specific spot to enable TPM in these settings will vary wildly by manufacturer, so you should check the manual that came with your computer or motherboard (you can probably find it online on the manufacturer's website). Once here, you can also enable Secure Boot from the UEFI menus.
If your system only supports a firmware-based TPM, it might be referred to as iPPT if your computer has an Intel processor, or fTPM for AMD processors. This enables security features that can help protect your computer like encrypting your storage drives or using logins like fingerprints or facial recognition. This is only possible because there's a safe place on your computer to store the encryption keys or biometric data that wouldn't be safe to store otherwise.
More recently both AMD and Intel have begun implementing firmware TPM, or fTPM, solutions. For example, Intel's Platform Trust Technology, or PTT, found in some Intel chipsets, provides the same TPM security protocols without the need for an additional physical chip. To your operating system and applications, PTT looks and acts exactly like TPM.
The difference is, computers with Intel PTT, or AMD's built-in firmware version, don't require a dedicated crypto-processor or memory. TPM or Trusted Platform Module 2.0 is a dedicated physical security chip that provides security against various modern-day attacks. Although installing a TPM 2.0 device manually is possible, most present days' motherboards have this module in built. As Windows 11 requires TPM 2.0 to be installed, the it displays this error when you do not have it yet. SpecificationTPM 1.2TPM 2.0ArchitectureThe one-size-fits-all specification consists of three parts.A complete specification consists of a platform-specific specification which references a common four-part TPM 2.0 library.